Difference between revisions of "Political Aspects"
Carmel Roche (talk | contribs) |
|||
| (8 intermediate revisions by 4 users not shown) | |||
| Line 1: | Line 1: | ||
<br><br> | <br><br> | ||
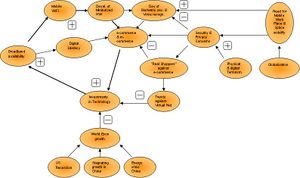
[[Image: | [[Image:SD_more_of_the_same.jpg|thumb|'''Figure 1.''' Systems Diagram: More of the Same]] | ||
<br> | <br> | ||
After the end of the cold war, the power of balance shifted from Russo-Americana to Pax Americana in 1980's. The Internet developed corresponding to this change in the balance of power resulting in the USA becoming the dominant player online. The Internet developed as the "information super highway" for the military in America. Politics played a major role in the Internet. However, in 2000's, the penetration of the Internet globally as well as the emergence of China as an economic power drives the end of the Pax Americana on the Internet. As a result, the political role on the Internet becomes more complicated and sensitive. | |||
'''International Regulations and Cyber Terrorism''' | |||
Cyber terrorism is the crucial constraint for the development of Internet technology. Many governments have tried to prevent the emergency problem. The WWW is the transnational platform for terrorists, governments realise the need for international regulations and consensus to confront cyber terrorism as well as cooperating with other countries. European Union countries concluded the " Treaty for Cyber Crime" in November 2001, so as to prevent further online terrorism and crime. The treaty articulates; | |||
1. Propostion of the framework for the international regulation and the foundation of international cooperation regime for preventing cyber terrorism, | |||
2. Proposition of crime tracking for signed countries, | |||
3. Unification of practices in criminal investigation and the definition of "cyber crime and terrorism". | |||
Many countries have registered the treaty, but the substantial criminal law in each country has not yet caught up to the reality of cyber crime and terrorism. Governments will seek international cooperation efficiently, however, most of the cyber crime increases at the rate of the status quo. The US may promptly develop regulations and technologies to prevent the terrorism independently. As a result "DIGITAL DIVIDE AMONG COUNTRIES" will gradually expand between developed and developing countries, whilst the use of the Internet increases exponentially. | |||
<br>[[Image:Cyberterror.jpg]] <br><br> | |||
In our scenario, the situation may not change in 10 years time. Because the Digital Divide among countries gradually expands, cyber terrorism and crime will increase gradually. And the hammer and nail situation between government and hacker remain same until 2015. Companies may suffer from cyber terrorism attacks, but the damage may be limited thanks to the firewall system. Individuals may suffer from virus, spam mails and so on, but many will have sophisticated software for the prevention of attacks. In developing countries, the situation may become more serious. The developing countries and their IPs may still be the breeding area for cyber terrorism, and the tracking may be difficult due to less development in technology infrastructure against cyber terrorism. Also, businesses and individuals may be vulnerable against these attack in these countries, due to the lack of regulations and technology. Only a few developing countries, such as Malaysia and China, where government develops the multimedia area for inducing investment from foreign countries, may enjoy the increase of FDI into the IT industry. As a result, the international cooperation against cyber terrorism and crime has not yet been formulated. Governments will respectively confront the issues, although talk on conference and exchange in information may gradually increase. | |||
'''China Factor''' | |||
In China, the user of the Internet drastically increased in recent years. In 1997, there were only 620,000 users in China, but in 2002, the number sharply increased to 33,700,000. (http://www.rand.org/publications/MR/MR1543/ ) In China, goverment censorship focused more on the broadcasting pages rather than porn sites, according to the BBC. (http://news.bbc.co.uk/2/low/technology/2540309.stm ) In 2002, China blocks 19,032 sites from all over the world, including BBC, CNN, Google. The reason why the government did so was that it was afraid of a revolution driven by the information delusion. The Eastern European countries in 1980 are a good example. The fall of the Berlin wall was driven by the US military radio broadcasting. The information shook up people and let them know the situation in the West, as well as the free atmosphere, so that the revolution process was amplified. In that context, the Internet plays a major role in alertness. However, the Chinese government now takes a moderate, gradual policy on the Internet. According to Sho-Kin-Shei, the head of Infomation and Industry department in China, China will concentrate on fostering people who can manage the Internet, resolving the digital divide regardless of income level, and establishing standards and technologies. Sho also mentioned the future of the Internet in china and regulating access to websites as "inappropriate sites" should be more restrictive than ever before to provide "proper information" to the people. | |||
Although technology and engineers may change the method and form of Internet usage, Internet content will remain the same due to regulations. | |||
<br><br> | |||
Back the our front page: [[Group 5: More of the Same]] | |||
Latest revision as of 11:57, 23 December 2004
After the end of the cold war, the power of balance shifted from Russo-Americana to Pax Americana in 1980's. The Internet developed corresponding to this change in the balance of power resulting in the USA becoming the dominant player online. The Internet developed as the "information super highway" for the military in America. Politics played a major role in the Internet. However, in 2000's, the penetration of the Internet globally as well as the emergence of China as an economic power drives the end of the Pax Americana on the Internet. As a result, the political role on the Internet becomes more complicated and sensitive.
International Regulations and Cyber Terrorism
Cyber terrorism is the crucial constraint for the development of Internet technology. Many governments have tried to prevent the emergency problem. The WWW is the transnational platform for terrorists, governments realise the need for international regulations and consensus to confront cyber terrorism as well as cooperating with other countries. European Union countries concluded the " Treaty for Cyber Crime" in November 2001, so as to prevent further online terrorism and crime. The treaty articulates; 1. Propostion of the framework for the international regulation and the foundation of international cooperation regime for preventing cyber terrorism, 2. Proposition of crime tracking for signed countries, 3. Unification of practices in criminal investigation and the definition of "cyber crime and terrorism".
Many countries have registered the treaty, but the substantial criminal law in each country has not yet caught up to the reality of cyber crime and terrorism. Governments will seek international cooperation efficiently, however, most of the cyber crime increases at the rate of the status quo. The US may promptly develop regulations and technologies to prevent the terrorism independently. As a result "DIGITAL DIVIDE AMONG COUNTRIES" will gradually expand between developed and developing countries, whilst the use of the Internet increases exponentially.

In our scenario, the situation may not change in 10 years time. Because the Digital Divide among countries gradually expands, cyber terrorism and crime will increase gradually. And the hammer and nail situation between government and hacker remain same until 2015. Companies may suffer from cyber terrorism attacks, but the damage may be limited thanks to the firewall system. Individuals may suffer from virus, spam mails and so on, but many will have sophisticated software for the prevention of attacks. In developing countries, the situation may become more serious. The developing countries and their IPs may still be the breeding area for cyber terrorism, and the tracking may be difficult due to less development in technology infrastructure against cyber terrorism. Also, businesses and individuals may be vulnerable against these attack in these countries, due to the lack of regulations and technology. Only a few developing countries, such as Malaysia and China, where government develops the multimedia area for inducing investment from foreign countries, may enjoy the increase of FDI into the IT industry. As a result, the international cooperation against cyber terrorism and crime has not yet been formulated. Governments will respectively confront the issues, although talk on conference and exchange in information may gradually increase.
China Factor
In China, the user of the Internet drastically increased in recent years. In 1997, there were only 620,000 users in China, but in 2002, the number sharply increased to 33,700,000. (http://www.rand.org/publications/MR/MR1543/ ) In China, goverment censorship focused more on the broadcasting pages rather than porn sites, according to the BBC. (http://news.bbc.co.uk/2/low/technology/2540309.stm ) In 2002, China blocks 19,032 sites from all over the world, including BBC, CNN, Google. The reason why the government did so was that it was afraid of a revolution driven by the information delusion. The Eastern European countries in 1980 are a good example. The fall of the Berlin wall was driven by the US military radio broadcasting. The information shook up people and let them know the situation in the West, as well as the free atmosphere, so that the revolution process was amplified. In that context, the Internet plays a major role in alertness. However, the Chinese government now takes a moderate, gradual policy on the Internet. According to Sho-Kin-Shei, the head of Infomation and Industry department in China, China will concentrate on fostering people who can manage the Internet, resolving the digital divide regardless of income level, and establishing standards and technologies. Sho also mentioned the future of the Internet in china and regulating access to websites as "inappropriate sites" should be more restrictive than ever before to provide "proper information" to the people.
Although technology and engineers may change the method and form of Internet usage, Internet content will remain the same due to regulations.
Back the our front page: Group 5: More of the Same